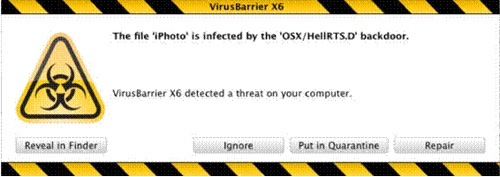
Intego (http://www.intego.com), a Mac security specialist, says it’s has discovered a new variant of a malware for Mac, called HellRTS, which, when installed on computers running Mac OS X, opens a backdoor that allows remote users to take control of infected Macs and perform actions on them.
Intego identifies this backdoor as OSX/HellRTS.D, a variant of an early Mac OS X malware first spotted in 2004. HellRTS, built in RealBasic, and a Universal Binary able to run on both PowerPC- and Intel-Based Macs, is able to perform a number of operations if installed on a Mac.
It sets up its own server and configures a server port and password. It duplicates itself, using the names of different applications, adding the new version to a user’s login items, to ensure that it starts up at login. (These different names can make it hard to detect, not only in login items, but also in Activity Monitor.) Intego says OSX/HellRTS.D can send e-mail with its own mail server, contact a remote server, and provide direct access to an infected Mac. It can also perform a number of operations such as providing remote screen-sharing access, shutting down or restarting a Mac, accessing an infected Mac’s clipboard, and much more.
This backdoor requires installation on a Mac, which could be carried out via a Trojan horse, or by exploiting a vulnerability in a program that accesses the Internet (such as a web browser). While Intego hasn’t found any instances of Macs being infected by this in the wild, the fact that this malware is being distributed on a number of forums shows that it will be accessible to a large number of malicious users who may attempt to use it to attack Macs. And Intego points out that its own VirusBarrier X6 detects and eradicates this malware, which it identifies it as OSX/HellRTS.D, with its threat filters dated April 15 or later.